CPABE TOOLKIT DOWNLOAD
Description The cpabe toolkit provides a set of programs implementing a ciphertext-policy attribute-based encryption scheme. The decrypted file will share the name with the encrypted file minus the. The following persons have directly or indirectly contributed code or ideas to the Advanced Crypto Software Collection. All they need is the public key, then can use cpabe-enc to encrypt it under a specified policy. HR employees have the "Human Resources" attribute tied to their private keys, and Executive employees have the "Executive" attribute tied to their private keys. July 21, Pairing-based cryptography PBC is a relatively young area of cryptography that revolves around a certain function with special properties. 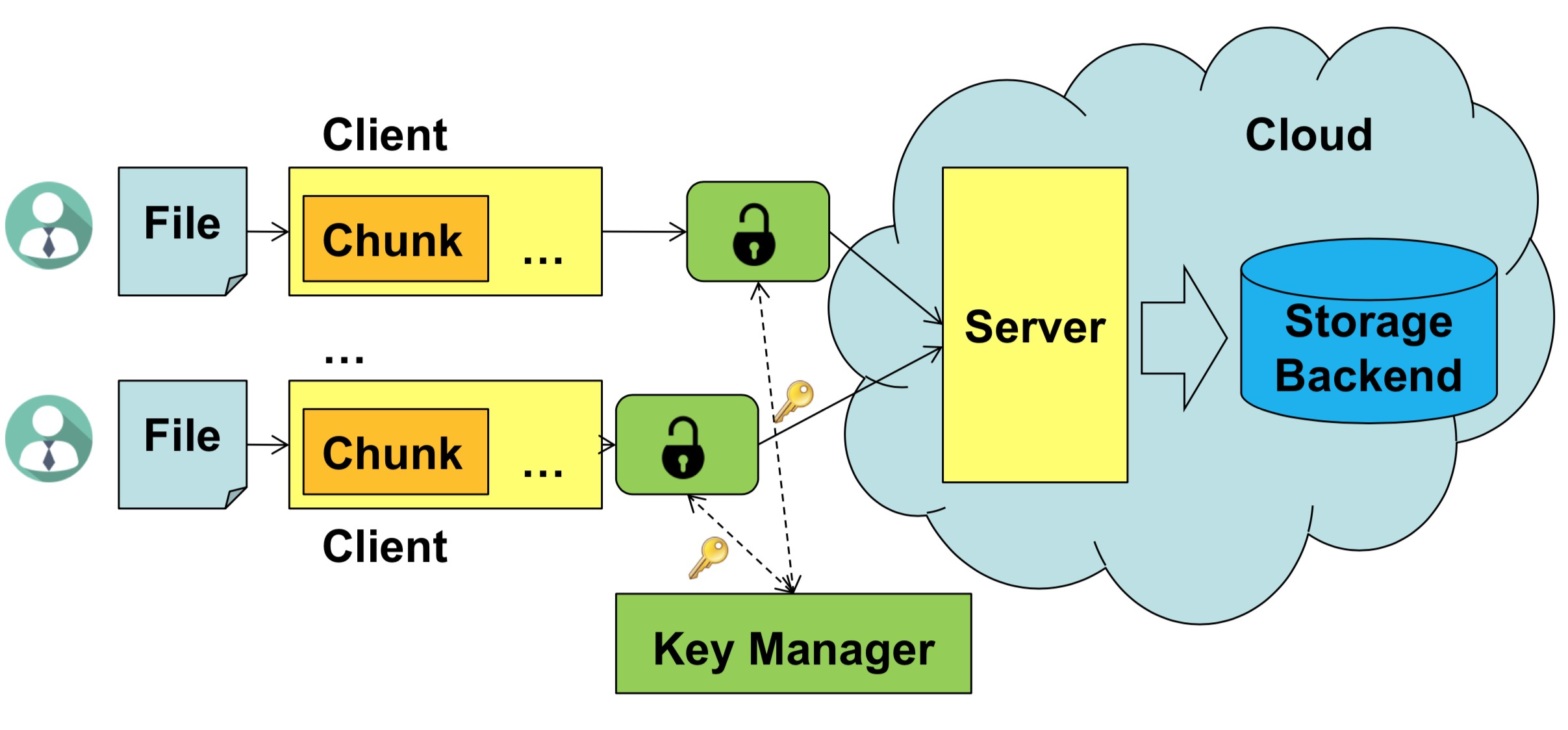
| Uploader: | Kigaktilar |
| Date Added: | 19 March 2017 |
| File Size: | 52.16 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 17660 |
| Price: | Free* [*Free Regsitration Required] |
March 28th, Proxy re-encryption is a form of public-key encryption that allows a user Alice to "delegate" her decryption rights to another user Bob.
Description The cpabe toolkit provides a set of programs toolkjt a ciphertext-policy attribute-based encryption scheme. March, Charm is a framework for rapidly prototyping advanced cryptosystems. December 1, Last updated: July 28, A broadcast encryption scheme allows a broadcaster to send an encrypted message to a set of receivers S, each of which has a different private key.
The best answers are voted up and rise to the top. The encryption itself serves as the RBAC mechanism.
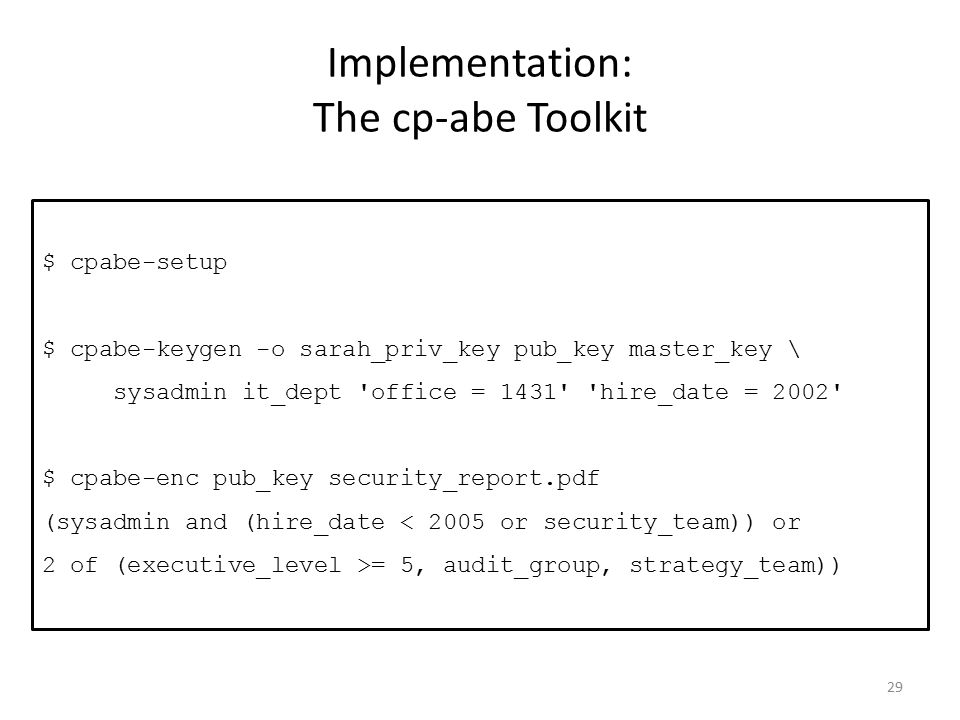
April 3, Last updated: The challenge is to construct a scheme which has communication sublinear in the number of receivers. For example, AutoBatch is an automated tool for finding efficient batch verification algorithms from high-level descriptions of digital signature schemes. Also, man pages for each of the four programs in the toolkit are toopkit online. As you can see in those examples, some attributes are assigned a value, while others a key simply "has" without further qualification.
Broadcast Encryption [external] Developers: The Projects Listed below are the current projects along with short descriptions. Papers The scheme is implemented as described in the following paper. Sign up or log in Sign up using Google. To try out the tools, take a look at the quickstart tutorial.
This library includes public key encryption schemes, identity-based encryption schemes, attribute-based encryption schemes, digital signatures, privacy-preserving signatures, commitment schemes, zero-knowledge proofs, and interactive protocols such as anonymous credential and oblivious transfer schemes. The PBC library Pairing-Based Cryptography library is a high performance C library built on top of the GMP library that contains routines which aid the implementation of pairing-based cryptosystems, including curve generation and pairing computation.
The decrypted file will share the name with the encrypted file minus the.
Ciphertext-Policy Attribute-Based Encryption (CPABE)
Unicorn Meta Zoo 9: John Bethencourt worked with Amit Sahai advisor and Brent Waters advisor on the CPABE toolkitan implementation of the ciphertext-policy attribute-based encryption scheme presented in their paper. Toolkiit known, but like many other things on the ACSC this is research quality software and should not be used in any application actually requiring security.
The example presented on the website presents a ciphertext encrypted such that only employees with the attributes "Human Resources" UNION "Executive" are able to decrypt it.
Sign up to join this community. However, this prevents the common practice of encrypting it on disk under a passphrase. September 12, Last updated: May tookkit, OpenABE is a cryptographic library that incorporates a variety of attribute -based encryption ABE algorithms, industry standard cryptographic functions and tools, and an intuitive application programming interface.
Advanced Crypto Software Collection
In addition to the compressed binary representation, the public key also contains legible parameters: Charm uses a hybrid design: The toolki was developed by several different contributors, who are credited along with the project descriptions.
The toolkit provides four command line tools used to perform the various operations of the scheme. Advanced Crypto Software Collection. It supports both content-based i. March, The AutoTools project is a collection of automated compilers for performing various cryptographic design tasks.

Comments
Post a Comment